
Vaultody MPC Core
Our Institutional-Grade Multi-Party Computation Technology
Empower your organization with proprietary Multi-Party Computation (MPC) technology built for institutional digital asset management. Vaultody MPC Core delivers advanced cryptographic protection while keeping control, governance, and custody entirely in your hands. Vaultody provides the technology - never the custody.
Share the Trust, Guard the Keys
Proprietary MPC Engine for Enterprise Digital Asset Control
Vaultody’s in-house developed MPC protocol redefines how institutions secure and govern blockchain assets. Unlike outsourced MPC providers, our architecture operates entirely within your environment, ensuring you maintain full authority over key generation, transaction signing, and policy management. Vaultody enables asset managers, exchanges, and financial platforms to achieve bank-grade security and compliance without giving up ownership or operational autonomy.
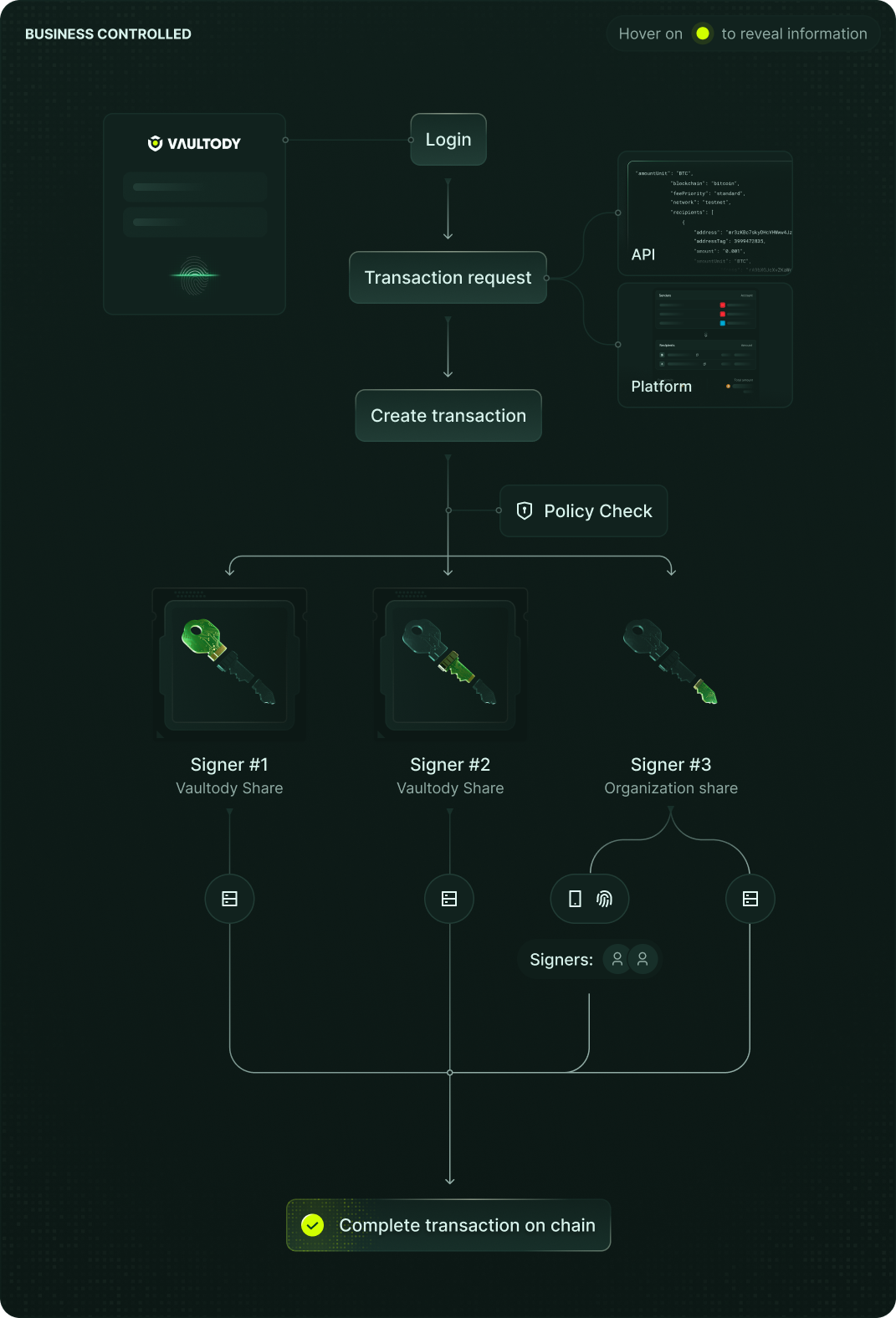
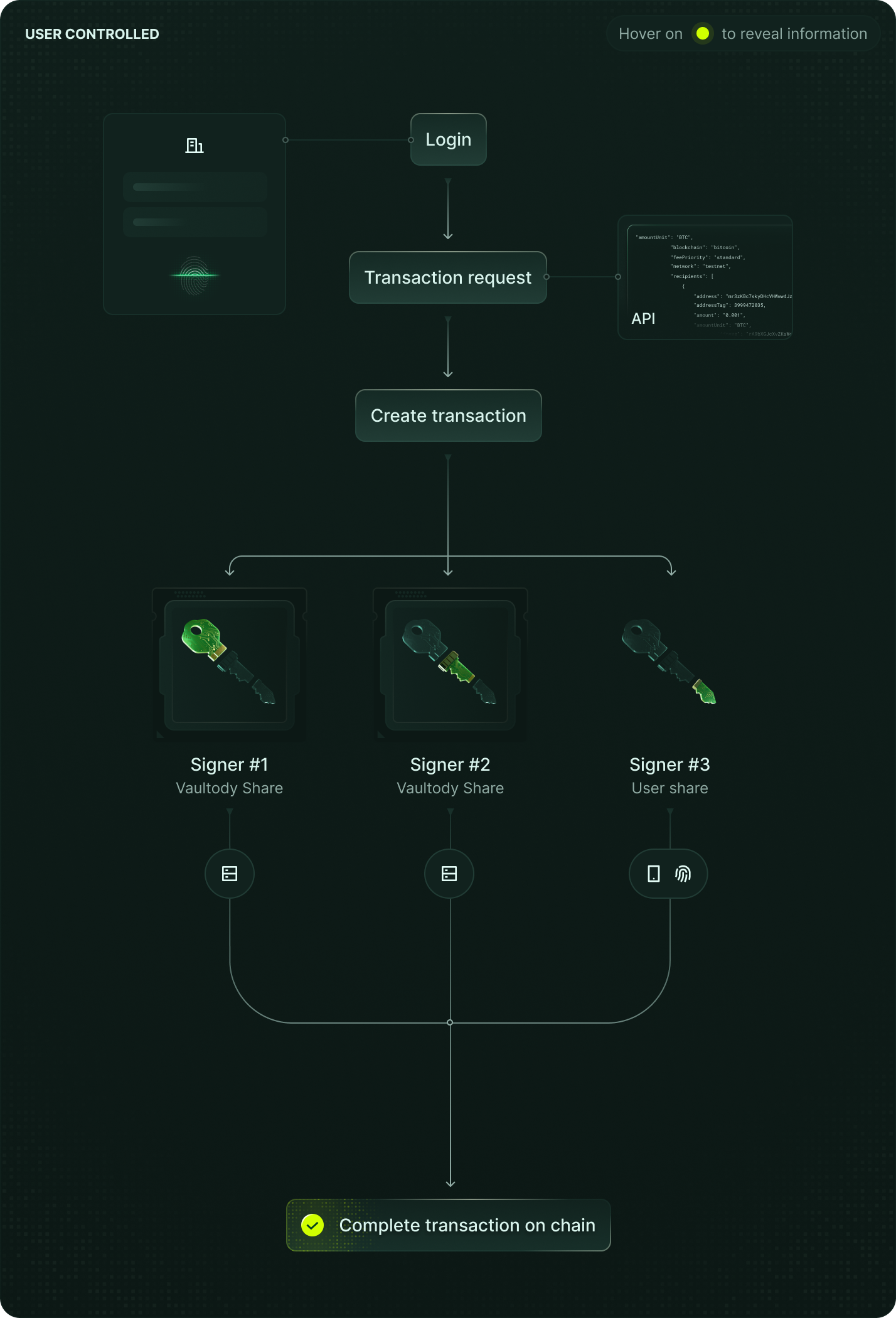
Distributed Cryptography and Threshold Signing
Vaultody MPC divides each cryptographic key into encrypted fragments stored across independent, hardened nodes. No single node ever holds the full key. Transactions are approved through threshold signature technology, ensuring every authorization meets your internal governance standards.
Decentralized Key Management
Encrypted key fragments, never a complete key in one place.
Flexible Threshold Signing
Custom threshold signing scheme.
Policy Integration
Instant controls for whitelists, limits, and governance.

Cross-Chain Compatibility
Works seamlessly across multiple networks and asset types.

Hardware-Backed Non-Custodial Protection
Vaultody’s MPC engine integrates with Hardware Security Modules (HSMs) for maximum cryptographic assurance. Key fragments are generated and processed within secure hardware boundaries under your control.
Through our non-custodial model, you maintain exclusive access to keys, transactions, and operational policies.
Vaultody supports policy automation, real-time monitoring, and high-volume transaction scalability while meeting global compliance requirements.

Why Leading Institutions Choose Vaultody
Complete Control
Define signing thresholds, approval policies, and node deployments to fit your governance framework.

Compliance-Ready
Every signature and approval is logged, auditable, and traceable for regulatory verification.

Scalable Security
Adapt key-sharing structures and user permissions as your organization grows.

Operational Sovereignty
Vaultody acts as your infrastructure partner - not a custodian. You retain full control, free from vendor lock-in or shared custody risks.
Experience the Vaultody Difference
Vaultody transforms MPC cryptography into a trusted foundation for secure and compliant digital asset operations.

No outsourced custody

No shared keys or dependencies

Security and compliance built within your organization

Direct Custody

Treasury Management

Wallet as a Service

Tokenizations
Coming Soon
Stable-coins Operations
Coming Soon
Direct Custody

Treasury Management

Wallet as a Service

Tokenizations
Coming Soon
Stable-coins Operations
Coming Soon
Share the Trust Guard the Keys
Custody stays with you. Security starts here.
Talk to our team to see how Vaultody MPC Core empowers your platform to share trust, guard keys, and own your digital asset future.
